It sounds easy – "just verify people's age before they access the service" – but whether we're talking about porn in the US or Australia's

NEWS BRIEF Cybercriminals have picked up a new tactic, impersonating CrowdStrike recruiters in order to distribute a cryptominer on their victims’ devices. This malicious campaign

Social Engineering – Techniken Social Engineering hat sich für Cyberkriminelle als besonders erfolgreich erwiesen, wenn es darum geht in Unternehmen einzudringen. Sobald ein Angreifer das

Federal authorities have arrested and indicted a 20-year-old U.S. Army soldier on suspicion of being Kiberphant0m, a cybercriminal who has been selling and leaking sensitive

Ever wonder how those “free” browser extensions that promise to save you money actually work? We dive deep into the controversial world of Honey, the

Cybersecurity researchers are warning of a new stealthy credit card skimmer campaign that targets WordPress e-commerce checkout pages by inserting malicious JavaScript code into a
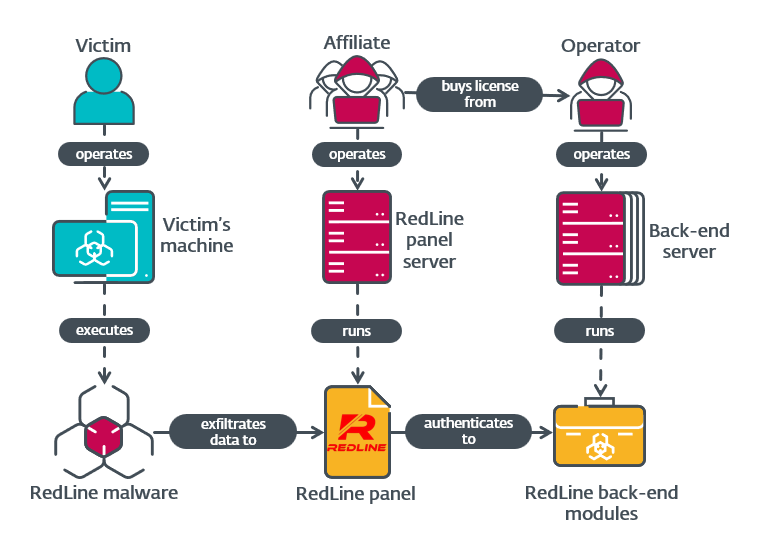
UPDATE (November 12th, 2024): We clarified the information in the fourth paragraph to better reflect RedLine’s functionality before versus after the takedown. On October 28th,

This week I'm giving a little teaser as to what's coming with stealer logs in HIBP and in about 24 hours from the time of

A Chinese threat actor is once again exploiting Ivanti remote access devices at large. If you had a nickel for every high-profile vulnerability affecting Ivanti

Payback Welches Thema ist aus Ihrer Sicht aktuell das wichtigste in Sachen Cybersicherheit? Sayed: Es gibt sicherlich mehrere relevante Themen, aber Informationssicherheit basiert nach wie
